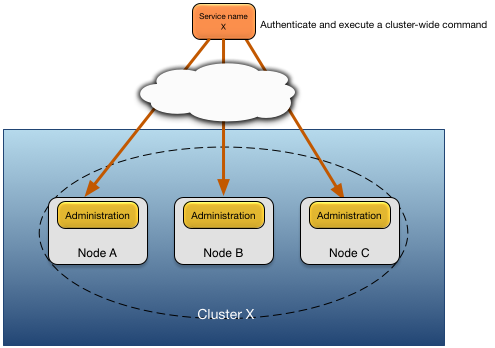
Administrative commands issued to multiple nodes using a partially qualified service name must use one of these authentication mechanisms:
the principal and credential provided to the administrative command must be defined on all targeted nodes.
the target nodes for the administrative command must have the client host on which the administration command is being executed defined as a trusted host (see the section called “Trusted hosts”).
The choice of authentication mechanism is dependent on local security polices and whether the application is deployed into a trusted network. For example, the use of trusted host authentication would not be appropriate on an untrusted network.
Figure 5.2, “Cluster authentication model” shows the use of common principal and credential information in a cluster.