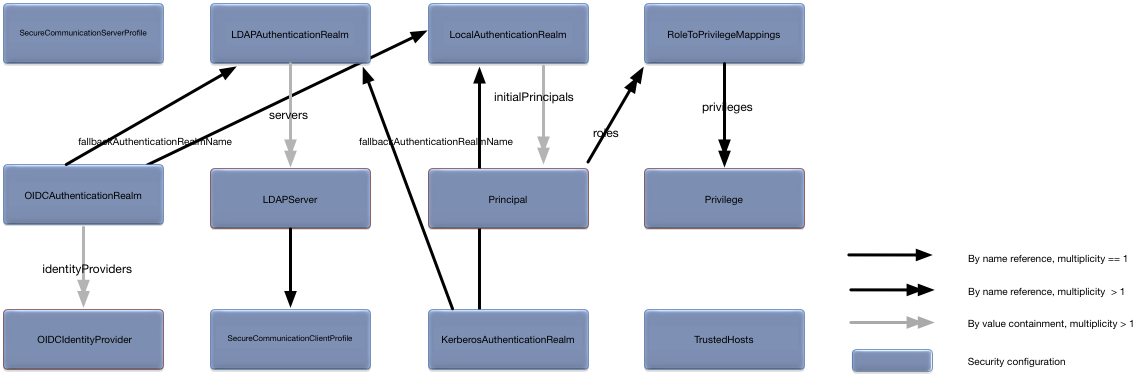
This section provides a detailed description of all security configuration. A snippet is provided for each configuration object showing the syntax for specifying all of the configuration values.
Security configuration has a configuration type of
com.tibco.ep.dtm.configuration.security.
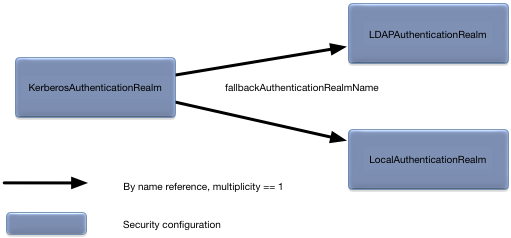
The KerberosAuthenticationRealm root
configuration object defines Kerberos authentication for a node. There
can only be a single KerberosAuthenticationRealm
defined on a node.
Figure 5.11, “KerberosAuthenticationRealm relationships” shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.1, “KerberosAuthenticationRealm object properties” and a snippet for these properties is in Example 5.1, “KerberosAuthenticationRealm object snippet”.
Table 5.1. KerberosAuthenticationRealm object properties
Example 5.1. KerberosAuthenticationRealm object snippet
name = "kerberos-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
KerberosAuthenticationRealm =
{
name = "my-kerberos-authentication-realm"
requireTrustedHostMembership = false
fallbackAuthenticationRealmName = "my-local-realm"
internalClientLoginConfigurationFile = "/opt/kerberos/client-configuration"
internalClientKeytabFile = "/opt/kerberos/keytab/client"
internalClientPrincipalName = "client-principal@ACME.COM"
jaasDebug = false
kerberosConfigurationFile = "/opt/kerberos/kerberos-configuration"
serverKeytabFile = "/opt/kerberos/keytab/server"
serverPrincipalName = "HTTP/my.host.com@ACME.COM"
ticketCacheFile = "/opt/kerberos/ticket/cache/file"
}
}
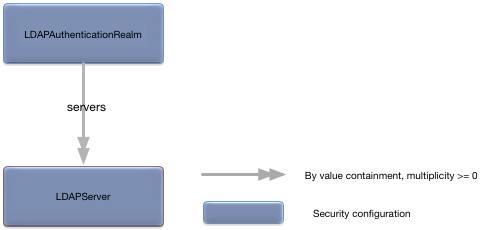
The LDAPAuthenticationRealm root
configuration object defines LDAP integration for a node. Figure 5.12, “LDAPAuthenticationRealm relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.2, “LDAPAuthenticationRealm object properties” and a snippet for these properties is in Example 5.2, “LDAPAuthenticationRealm object snippet”.
Table 5.2. LDAPAuthenticationRealm object properties
Example 5.2. LDAPAuthenticationRealm object snippet
name = "ldap-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LDAPAuthenticationRealm =
{
name = "my-ldap-authentication-realm"
requireTrustedHostMembership = true
allowSecureCommunicationClientAuthentication = true
requirePassword = false
servers =
[
{ ... }
{ ... }
]
}
}
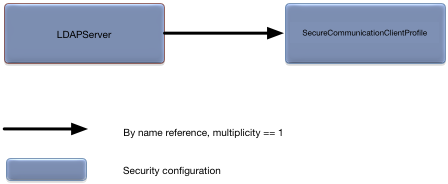
The LDAPServer configuration object
defines LDAP server configuration. Figure 5.13, “LDAPServer relationships” shows the relationships to
other configuration objects.
A detailed description of the configuration object properties is in Table 5.3, “LDAPServer object properties” and a snippet for these properties is in Example 5.3, “LDAPServer object snippet”.
Table 5.3. LDAPServer object properties
| Name | Type | Description |
| String | LDAP server host name. Optional. Default value is
localhost. |
| Short | LDAP server port number. Optional. Default value is
389. |
| Enumeration with these valid values,
BIND,
LOCAL_PASSWORD_COMPARE, and
REMOTE_PASSWORD_COMPARE. | The type of authentication to perform.
BIND authenticates principals by connecting
to the LDAP server using the principal name and credentials.
LOCAL_PASSWORD_COMPARE authenticates
principals by connecting to the LDAP server using the system
principal, searching for the user, retrieving its password
attribute, and comparing the values locally with the principal's
credentials. REMOTE_PASSWORD_COMPARE is the
same as LOCAL_PASSWORD_COMPARE except that
the comparison is performed by the LDAP server. Optional.
Default value is BIND. |
| String | The password attribute for this LDAP server's principals.
Optional. Default value is
userPassword. |
| String [ ] | A list of Distinguished Names under which principals are searched for during search-based authentication operations or user name to Distinguished Name conversions. Required. Must contain at least on element. |
| String | The LDAP filter expression used when searching for
principals. The filter permits Java pattern substitution
expressions. {0} is bound to the input
principal and {1} is bound to its
corresponding distinguished name. Optional. Default value is
CN={0}. |
| String [ ] | A list of Distinguished Names under which roles are
searched for. Optional. Default value is the
principalSearchRoots value. |
| String | The LDAP filter expression used when searching for roles
of which a principal is a member. The filter permits Java
pattern substitution expressions. {0} is
bound to the input principal and {1} is bound
to its corresponding Distinguished Name. Optional. Default value
is roleOccupant={1}. |
| String | Attribute of a role entry that is used to map to
privileges. Optional. Default value is
CN. |
| String | Name of a secure communication client profile to use when configuring secure communications with an LDAP server. Optional. No default value. If not set LDAP server connections are not secure. |
| String | The system principal password to log in to the LDAP
server to perform authentication operations. Opaque passwords
are generated using the epadmin secret
target. See the section called “secret target”.
Required. |
| String | The system principal to log in to the LDAP server to perform authentication operations. Required. |
Example 5.3. LDAPServer object snippet
name = "ldap-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LDAPAuthenticationRealm =
{
servers =
[
{
host = "ldap.primary.acme.com"
portNumber = 390
principalAuthenticationAlgorithm = LOCAL_PASSWORD_COMPARE
principalPasswordAttribute = "password"
principalSearchRoots = [ "ou=users,dc=example.dc=com" ]
principalSearchFilter = "cn={0}"
roleSearchRoots = [ "ou=roles,dc=example.dc=com" ]
roleSearchFilter = "membership={1}"
roleNameAttribute = "roleID"
secureCommunicationProfileName = "secure-ldap-client-profile"
systemPassword = "secret"
systemPrincipal = "cn=SBLDAPUser,cn=Users,dc=ldap,dc=example,dc=com"
}
{
host = "ldap.backup.acme.com"
portNumber = 390
principalAuthenticationAlgorithm = LOCAL_PASSWORD_COMPARE
principalPasswordAttribute = "password"
principalSearchRoots = [ "ou=users,dc=example.dc=com" ]
principalSearchFilter = "cn={0}"
roleSearchRoots = [ "ou=roles,dc=example.dc=com" ]
roleSearchFilter = "membership={1}"
roleNameAttribute = "roleID"
secureCommunicationProfileName = "secure-ldap-client-profile"
systemPassword = "secret"
systemPrincipal = "cn=SBLDAPUser,cn=Users,dc=ldap,dc=example,dc=com"
}
]
}
}
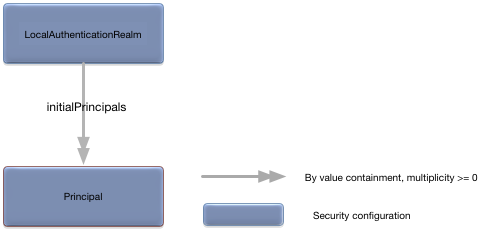
The LocalAuthenticationRealm foot
configuration object defines the characteristics and initial principals
in the local authentication realm for a node. Figure 5.14, “LocalAuthenticationRealm relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.4, “LocalAuthenticationRealm object properties” and a snippet for these properties is in Example 5.4, “LocalAuthenticationRealm object snippet”.
Table 5.4. LocalAuthenticationRealm object properties
| Name | Type | Description |
| Boolean | Automatically authenticate if user connecting over a
secure communication channel. A value of true
allows automatic authentication, a value of
false disables automatic authentication.
Optional. Default value is false. |
| | Initial set of principals (see the section called “Principal”) in this realm. The values in this field cannot change when this configuration is updated. If the values do change, configuration audit will fail. Optional. No default value. |
| String | Name of the authentication realm. This name must be unique across all authentication realms. Required. |
| Boolean | Require a password if user is connecting from a trusted
host unless automatically authenticated because of a secure
communication channel. A value of true
requires a password when connecting from a trusted host, a value
of false allows connection from a trusted
host without a password. Optional. Default value is
|
| Boolean | A value of true only allows users to
connect from a trusted host, a value of false
allows users to connect from any host. Optional. Default value
is |
Example 5.4. LocalAuthenticationRealm object snippet
name = "local-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LocalAuthenticationRealm =
{
name = "my-local-authentication-realm"
requireTrustedHostMembership = true
allowSecureCommunicationClientAuthentication = true
requirePassword = false
initialPrincipals =
[
{ ... }
{ ... }
]
}
}
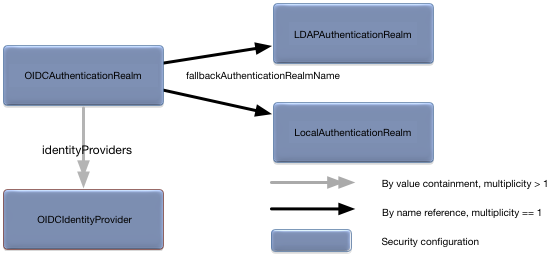
The OIDCAuthenticationRealm root
configuration object defines OpenId Connect authentication for a node.
Figure 5.15, “OIDCAuthenticationRealm relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.5, “OIDCAuthenticationRealm object properties” and a snippet for these properties is in Example 5.5, “OIDCAuthenticationRealm object snippet”.
Table 5.5. OIDCAuthenticationRealm object properties
| Name | Type | Description |
| String | The default address to redirect a user to after authentication if no redirect URL was provided in the authentication request. Optional. Default value is null. |
| Associative array of
OIDCIdentityProvider configuration objects
keyed by identity provider names. | An associative array of
OIDCIdentityProvider (see Table 5.6, “OIDCIdentityProvider object properties”)
configuration objects indexed by provider names. Provider names
must be URL safe and non-empty. Required. |
| String | The name of the realm used for all authorization. This
must be the name of an active
LDAPAuthenticationRealm or
LocalAuthenticationRealm. If the fallback
realm is not defined, configuration activation will fail.
Required. |
| String | Name of the authentication realm. This name must be unique across all authentication realms. Required. |
| Integer | The amount of time to wait for a provider's response in seconds before timing out. Optional. Default is 300 seconds. |
| Boolean | A value of true only allows users to
connect from a trusted host, a value of false
allows users to connect from any host. Optional. Default value
is |
Example 5.5. OIDCAuthenticationRealm object snippet
name = "oidc-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
OIDCAuthenticationRealm =
{
name = "my-oidc-authentication-realm"
requireTrustedHostMembership = false
defaultRedirectURL = "http://redirect.acme.com"
fallbackAuthenticationRealmName = "my-ldap-realm"
pendingAuthenticationTimeoutSeconds = 600
identityProviders =
{
"Google" = { ... }
"Auth0" = { ... }
}
}
}
The OIDCIdentityProvider object defines the configuration for OpenId Connect providers.
Support is provided for federated identity providers like Auth0.
Federated providers use subject prefixes to map to the actual provider
defined in this configuration. This mapping is configured using the
subjectProviderMappings configuration property. For
example:
//
// Subject provider mappings in Auth0 configuration
// A subject prefix of google-oauth2 maps to the
// configured "Google" identity provider
//
subjectProviderMappings =
{
"google-oauth2" = "Google"
}
//
// Auth0 identity contains "sub" claims
//
// The "|" is the delimiter, so "google-oauth2" is the prefix that
// identifies the actual provider providing the identity information.
// 105569619522230371597 is the subject for the principal from the identity
// provider represented by google-oauth2
//
sub: 'google-oauth2|105569619522230371597'
//
// The same principal authenticated directly against "Google"
// would have the same identity information in the "sub" field.
//
sub: '105569619522230371597'
Figure 5.16, “OIDCIdentityProvider relationships” shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.6, “OIDCIdentityProvider object properties” and a snippet for these properties is in Example 5.6, “OIDCIdentityProvider object snippet”.
Table 5.6. OIDCIdentityProvider object properties
| Name | Type | Description |
| String | The client's authentication identifier. Required |
| String | The client's authentication secret key. Opaque passwords
are generated using the epadmin secret
target. See the section called “secret target”.
Required. |
| String | The identity provider's Document Discovery URL for obtaining discovery information. Required. |
| String | The attribute in a given principal's ID Token to be used as the identity for this principal. Required. |
| Associative array of subject prefixes to identity provider names. | Map federated identity provider subject prefixes to
configured identity provider names. The provider names must be
configured in this configuration. This field is only valid for
federated identity providers like Auth0. Optional. Default is
null (no mappings). |
Example 5.6. OIDCIdentityProvider object snippet
name = "oidc-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
OIDCAuthenticationRealm =
{
identityProviders =
{
"Google" =
{
documentDiscoveryURL = "https://accounts.google.com/.well-known/openid-configuration"
clientID = "my-google-client-identifier"
clientSecret = "my-google-client-secret"
identityAttributeName = "email"
}
"Auth0" =
{
documentDiscoveryURL = "https://tibco.auth0.com/.well-known/openid-configuration"
clientID = "my-auth0-client-identifier"
clientSecret = "my-auth0-client-secret"
identityAttributeName = "email"
subjectProviderMappings =
{
"google-oauth2" = "Google"
}
}
}
}
}
The Principal configuration object
defines a principal managed by the local authentication realm. Figure 5.17, “Principal relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.7, “Principal object properties” and a snippet for these properties is in Example 5.7, “Principal object snippet”.
Table 5.7. Principal object properties
| Name | Type | Description |
| Boolean | Control whether the user account is locked. If
true the user account is locked and cannot be
accessed, if false the account is enabled and
can be accessed. Optional. Default value is
false. |
password | String | Opaque credential. Opaque text credentials are generated
using the epadmin secret target. See the section called “secret target”. Required. |
| Integer | An optional expiration time for the password in days. Default value is 0 (no expiration). |
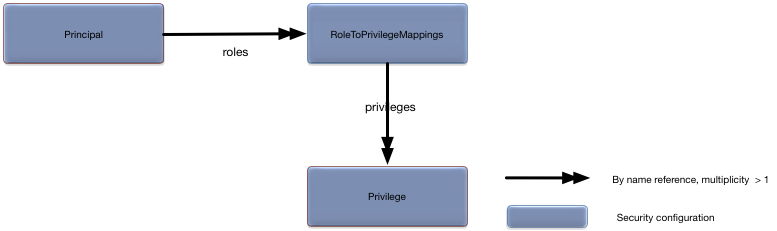
roles | String [ ] | An array of role names. Optional. No default. |
userName | String | Principal name. Required. |
Example 5.7. Principal object snippet
name = "local-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LocalAuthenticationRealm =
{
initialPrincipals =
[
{
userName = "FredTheAdministrator"
password = "LKJALISJDOIQUWEOIAJSLKDJALSJDL"
roles =
[
"administrator"
]
passwordExpirationPeriodDays = 12
locked = true
}
]
}
}
The RoleToPrivilegeMappings object
defines the roles and their associated privileges. Figure 5.18, “RoleToPrivilegeMappings relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.8, “RoleToPrivilegeMappings object properties” and a snippet for these properties is in Example 5.8, “RoleToPrivilegeMappings object snippet”.
Example 5.8. RoleToPrivilegeMappings object snippet
name = "my-target-role-mappings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
RoleToPrivilegeMappings =
{
privileges =
{
administrator = [ ... ]
monitor = [ ...]
}
}
}
The Privilege object defines
permissions for a resource. Figure 5.19, “Privilege relationships” shows the relationships to
other configuration objects.
A detailed description of the configuration object properties is in Table 5.9, “Privilege object properties” and a snippet for these properties is in Example 5.9, “Privilege object snippet”.
Example 5.9. Privilege object snippet
name = "my-target-role-mappings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
RoleToPrivilegeMappings =
{
privileges =
{
administrator =
[
{
resource = "mytarget.start"
privilege = "AdminRunCommand"
},
{
resource = "mytarget.stop"
privilege = "AdminRunCommand"
}
]
monitor =
[
{
resource = "mytarget.display"
privilege = "AdminRunCommand"
}
]
}
}
}
The SecureCommunicationClientProfile
root configuration object defines a secure communication profile for
client connectivity. Figure 5.20, “SecureCommunicationClientProfile relationships” shows
the relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.10, “SecureCommunicationClientProfile object properties” and a snippet for these properties is in Example 5.10, “SecureCommunicationClientProfile object snippet”.
Table 5.10. SecureCommunicationClientProfile object properties
| Name | Type | Description |
excludedCipherSuitePatterns | String [ ] | A list of Java regular expression patterns for excluded
cipher suites. This value is exclusive of the
includedCipherSuites property. Optional.
Default is
^.*_(MD5|(?<!TLS_DHE_RSA_WITH_AES_\\d\\d\\d_CBC_)SHA|SHA1)$
if no includedCipherSuites are
specified. |
includedCipherSuites | String [ ] | A list of allowed cipher suites. This value is exclusive
of the excludedCipherSuitePatterns property.
Optional. Default is the JRE's full set of supported cipher
suites. |
includedProtocols | String [ ] | A list of allowed protocols. Optional. Default is
TLSv1.1 and TLSv1.2. An
empty array uses the JRE's full set of supported
protocols. |
keyPassword | String | The password to access the key within the keystore.
Opaque text credentials are generated using the epadmin
secret target. See the section called “secret target”. Optional. Default is
keyStorePassword. |
keyStorePassword | String | Key store password, used to access the key store
contents. Opaque text credentials are generated using the
epadmin secret target. See the section called “secret target”. Required if
keyStore specified. |
keyStore | String | Absolute path to a key store file that contains the client's certificate as well as optional trust store information, depending on key store format. If the key store contains multiple private key entries (aliases), the first is used. This file must be valid on the machine where the client is running. If provided, clients can perform mutual authentication with a server. Optional. No default. |
keyStoreType | String | Key store type. Optional. Default is
jks. |
name | String | The name of the profile. This name must be unique across all secure communication profiles - both client and server. Required. |
requireClientAuthentication | Boolean | Enable (true) or disable
(false) required client authentication. If
enabled a keyStore must be configured to sign
the secure communication protocol handshake. Optional. Default
is false. |
trustStore | String | An absolute file path to the trust store used to verify client trust. This file must be valid on the machine where the client is running. Required. |
trustStorePassword | String | The password to access the trust store. Opaque text
credentials are generated using the epadmin
secret target. See the section called “secret target”. Required if
trustStore specified. |
trustStoreType | String | Trust store type. Optional. Default is
jks. |
Example 5.10. SecureCommunicationClientProfile object snippet
name = "my-secure-client-settings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
SecureCommunicationClientProfile =
{
name = "my-secure-client-profile"
keyStore = "/absolute/path/myKeyStore.jks"
keyStorePassword = "secret"
keyPassword = "anothersecret"
keyStoreType = "JCEKS"
trustStore = "/absolute/path/myTrustStore.jks"
trustStorePassword = "athirdsecret"
trustStoreType = "JCEKS"
requireClientAuthentication = true
excludedCipherSuitePatterns = [ "^.*_(MD5|SHA|SHA1)$" ]
includedProtocols = [ ] // use JRE's supported protocols
}
}
The SecureCommunicationServerProfile
root configuration object defines a secure communication profile for
listeners. Figure 5.21, “SecureCommunicationServerProfile relationships” shows
the relationships to other configuration objects.
A detailed description of the configuration object properties is in Table 5.11, “SecureCommunicationServerProfile object properties” and a snippet for these properties is in Example 5.11, “SecureCommunicationServerProfile object snippet”.
Table 5.11. SecureCommunicationServerProfile object properties
| Name | Type | Description |
excludedCipherSuitePatterns | String [ ] | A list of Java regular expression patterns for excluded
cipher suites. This value is exclusive of the
includedCipherSuites property. Optional.
Default is
^.*_(MD5|(?<!TLS_DHE_RSA_WITH_AES_\\d\\d\\d_CBC_)SHA|SHA1)$
if no includedCipherSuites are
specified. |
includedCipherSuites | String [ ] | A list of allowed cipher suites. This value is exclusive
of the excludedCipherSuitePatterns property.
Optional. Default is the JRE's full set of supported cipher
suites. |
includedProtocols | String [ ] | A list of allowed protocols. Optional. Default is
TLSv1.1 and TLSv1.2. An
empty array uses the JRE's full set of supported
protocols. |
keyPassword | String | The password to access the key within the keystore.
Opaque text credentials are generated using the epadmin
secret target. See the section called “secret target”. Optional. Default is
keyStorePassword. |
keyStorePassword | String | Key store password, used to access the key store
contents. Opaque text credentials are generated using the
epadmin secret target. See the section called “secret target”. Required. |
keyStore | String | Absolute path to a key store file that contains the server's certificate as well as optional trust store information, depending on key store format. If the key store contains multiple private key entries (aliases), the first is used. This file must be valid on the machine where the node is running. Required. |
keyStoreType | String | Key store type. Optional. Default is
jks. |
name | String | The name of the profile. This name must be unique across all secure communication profiles - both client and server. Required. |
requireClientAuthentication | Boolean | Enable (true) or disable
(false) required client authentication. If
enabled a trustStore must be configured to
verify client trust. Optional. Default is
false. |
subjectNameElementToUserNameMappings | Associative array of certificate based principal names to authorization user names. | A map whose keys are certificate-based principal names
and whose values are authorization user names. Used in cases
where an incoming client certificate is used for authentication,
but none of the elements of its subject name are suitable for
mapping to roles during authorization. Optional. No default,
subject name element extracted with the
userNameObjectIdentifierSearchPath must yield
a valid user name for authorization purposes. |
trustStore | String | An absolute file path to the trust store used to verify client trust. This file must be valid on the machine where the node is running. If provided, servers can perform mutual authentication with clients. Optional. |
trustStorePassword | String | The password to access the trust store. Opaque text
credentials are generated using the epadmin
secret target. See the section called “secret target”. Required if
trustStore specified. |
trustStoreType | String | Trust store type. Optional. Default is
jks. |
userNameObjectIdentifierSearchPath | String [ ] | An array of attribute keywords, or X.509 object
identifiers (OIDs), indicating the order in which the client's
X.509 certificate subject Distinguished Name attributes are
searched to find a user name for authorization purposes. This
key is only relevant if
requireClientAuthentication is enabled and a
trust store is present. Supported attribute keywords are
userID, CN,
emailAddress, and DN.
Optional. Default is the search order
emailAddress, CN,
DN. |
Example 5.11. SecureCommunicationServerProfile object snippet
name = "my-secure-server-settings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
SecureCommunicationServerProfile =
{
name = "my-secure-server-profile"
excludedCipherSuitePatterns = [ "^.*_(MD5|SHA|SHA1)$" ]
includedProtocols = [ ] // use JRE's supported protocols
keyPassword = "anothersecret"
keyStorePassword = "secret"
keyStore = "/absolute/path/myKeyStore.jks"
keyStoreType = "JCEKS"
requireClientAuthentication = true
subjectNameElementToUserNameMappings =
{
"subjectNameElementFoo" = "userNameFoo"
"subjectNameElementBar" = "userNameBar"
}
trustStore = "/absolute/path/myTrustStore.jks"
trustStorePassword = "athirdsecret"
trustStoreType = "JCEKS"
userNameObjectIdentifierSearchPath = [ "userID", "CN", "1.2.3.4", "DN" ]
}
}The TrustedHosts object defines trusted
hosts. Figure 5.22, “TrustedHosts relationships” shows the
relationships to other configuration objects.
Multiple TrustedHosts configuration objects
with different configuration names can be active at the same time. When
a configuration is activated, all hosts in the new configuration are
added to the trusted hosts for a node. When a configuration is
deactivated, all hosts in the configuration being deactivated are
removed from the trusted hosts for a node unless another active
TrustedHosts configuration also defined the host as
trusted.
A detailed description of the configuration object properties is in Table 5.12, “TrustedHosts object properties” and a snippet for these properties is in Example 5.12, “TrustedHosts object snippet”.
![[Warning]](images/warning.png) | |
IP addresses specified in the |
Example 5.12. TrustedHosts object snippet
name = "trusted-hosts"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
TrustedHosts =
{
hosts =
[
"host1",
"host2",
"*.some.domain.org",
"host4.tibco.com",
"189.4.5.6",
"192.168.2.0/24",
"201:db8::30:4/101",
"2601:646:4102:9184:d56c:b9bc:f9ed:1ee4%en1"
]
}
}