Security monitoring and administration is done from the node
Security tab. The following commands are accessed from
the Security tab.
AddLocalauthentication source. See the section called “Add user”.Export- export the node'slocalauthentication realm's user configuration. See the section called “Backing up a local authentication realm”.Remove- remove a user definition from the node'slocalauthentication realm. See the section called “Remove a user”.Reset- change a password in the node'slocalauthentication realm. See the section called “Change a password”.Update- update a user definition, other than password, in the node'slocalauthentication realm. See the section called “Update a user”.
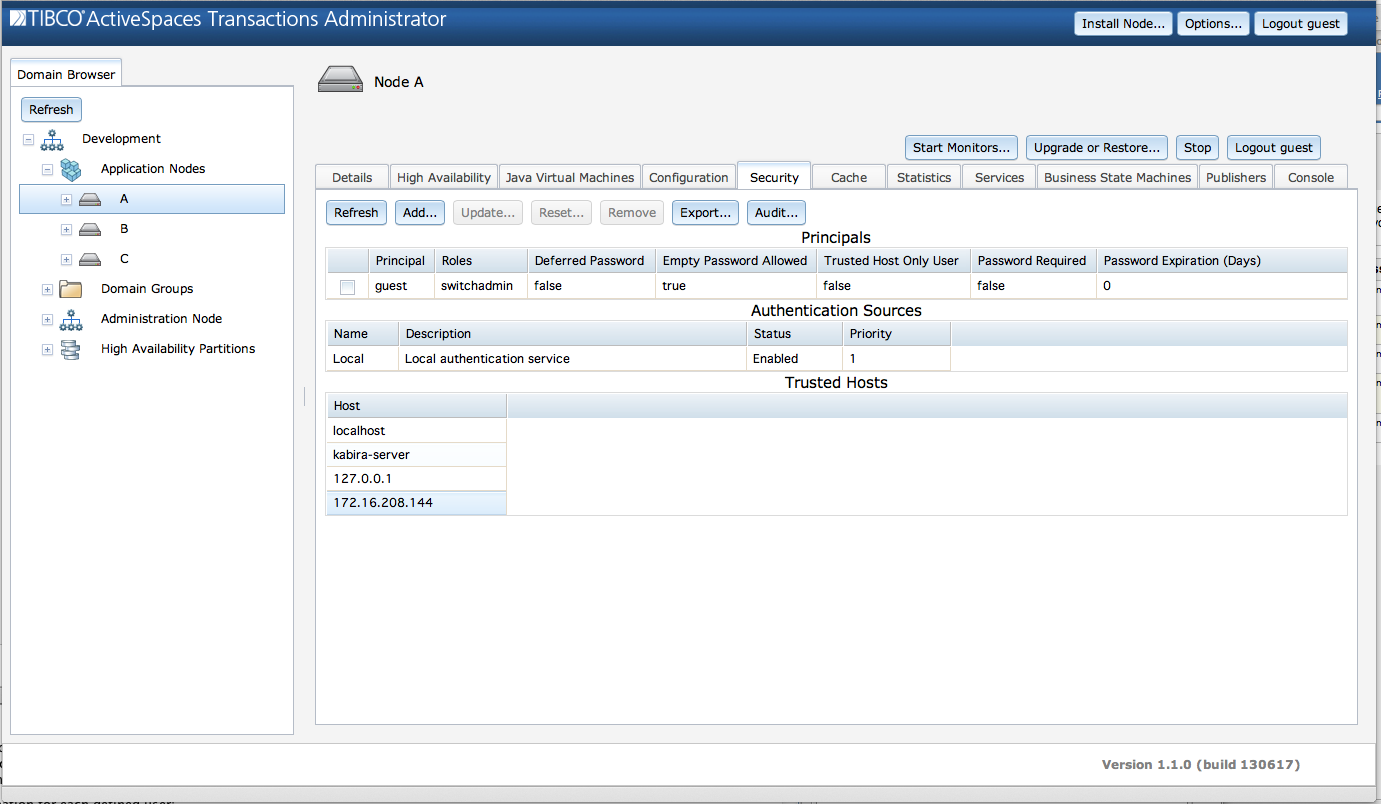
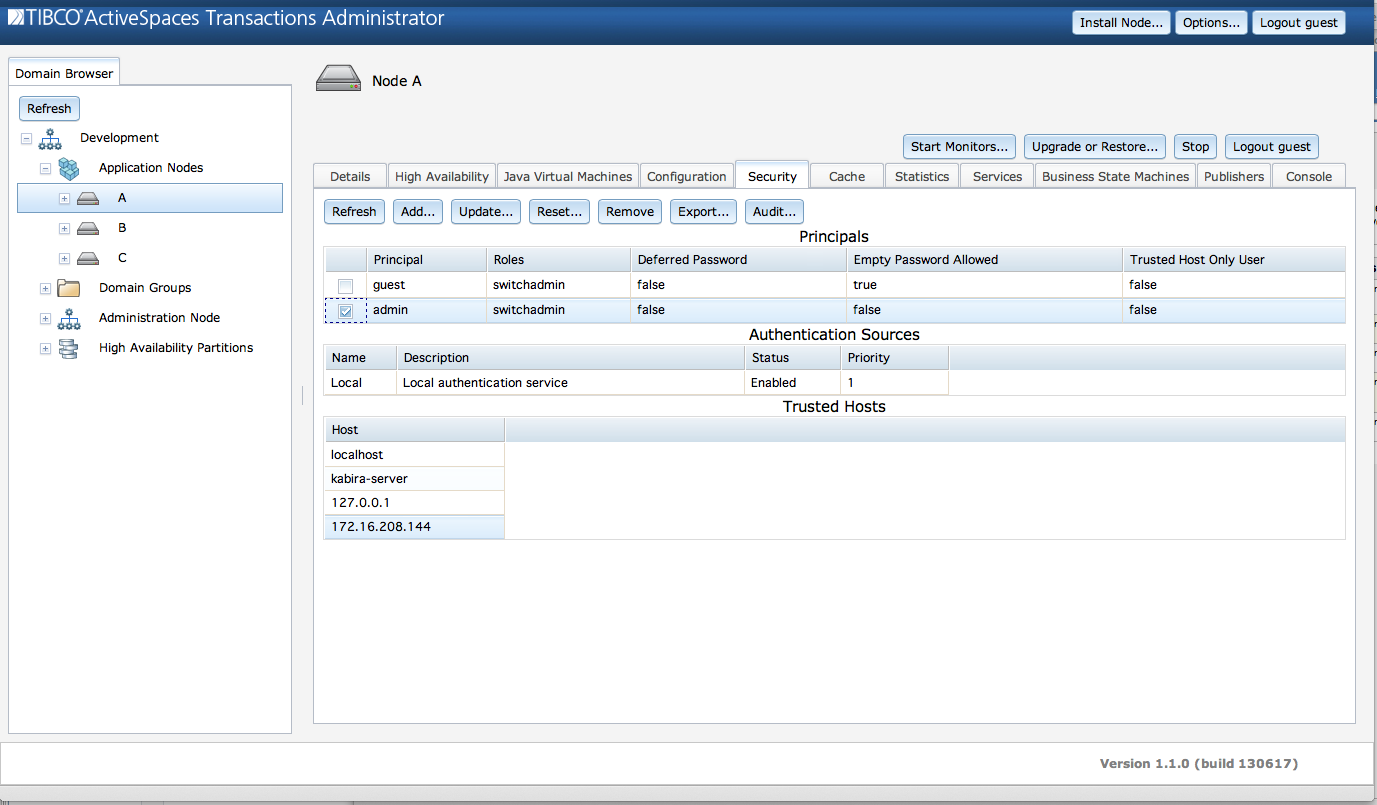
Figure 5.4, “Security information” shows the security
information displayed from the Security tab.
This screen consists of these sections:
Principals - all principals defined in the
localauthentication realm for this node.Authentication Sources - all realms being used by this node.
Trusted Hosts - the trusted hosts used by this node.
The Principals section shows this information for
each principal defined in the node's local
authentication source:
Realm Name - Realm in which user is defined.
User Name - Principal name.
Password Expiration (Days) - The password expiration time in days. A value of zero indicates that the password does not expire.
Account Locked -
trueif the user account is locked,falseif the account can still be accessed.Roles - Roles granted to this principal.
Authentication via Secure Communication Allowed - Is a password required when connecting over a secure communication channel?
Password Always Required - Is a password required even when connecting from a trusted host?
Trusted Host Membership Required of Client - Is user only allowed to connect from a trusted host?
This information can also be displayed using:
epadmin --servicename=<node-service-name> display user
The Authentication Sources section shows this
information for each configured authentication realm:
Realm Name - Authentication realm name.
Realm Type - Authentication realm type description.
Referenced By - List of entities using this realm.
This information can also be displayed using:
epadmin --servicename=<node-service-name> display realm
The Trusted Hosts section shows this information
for each trusted host:
Network Address - IP address for a trusted host.
Host Name - the host name for a trusted host. This field may be empty if a trusted network address cannot be resolved to a host name using a reverse Domain Name Service (DNS) lookup.
Source - the source of the trusted host. This field may contain one of:
default- this host was discovered using the local machine's network interfaces (see the section called “Trusted hosts”), for example::1.configured- this trusted host was an explicitly configured IPv4, IPv6, or FQDN network address (see the section called “TrustedHosts”), for examplemyhost.acme.com.a PQDN - this host is trusted because of a configured PQDN. The network address was resolved to a FQDN using a reverse DNS lookup and then matched to a PQDN, for example
*.acme.com.a CIDR block - this host is trusted because of a configured CIDR block. The network address is within the configured CIDR block, for example
192.168.2.0/24.
This information can also be displayed using:
epadmin --servicename=<node-service-name> display trusted
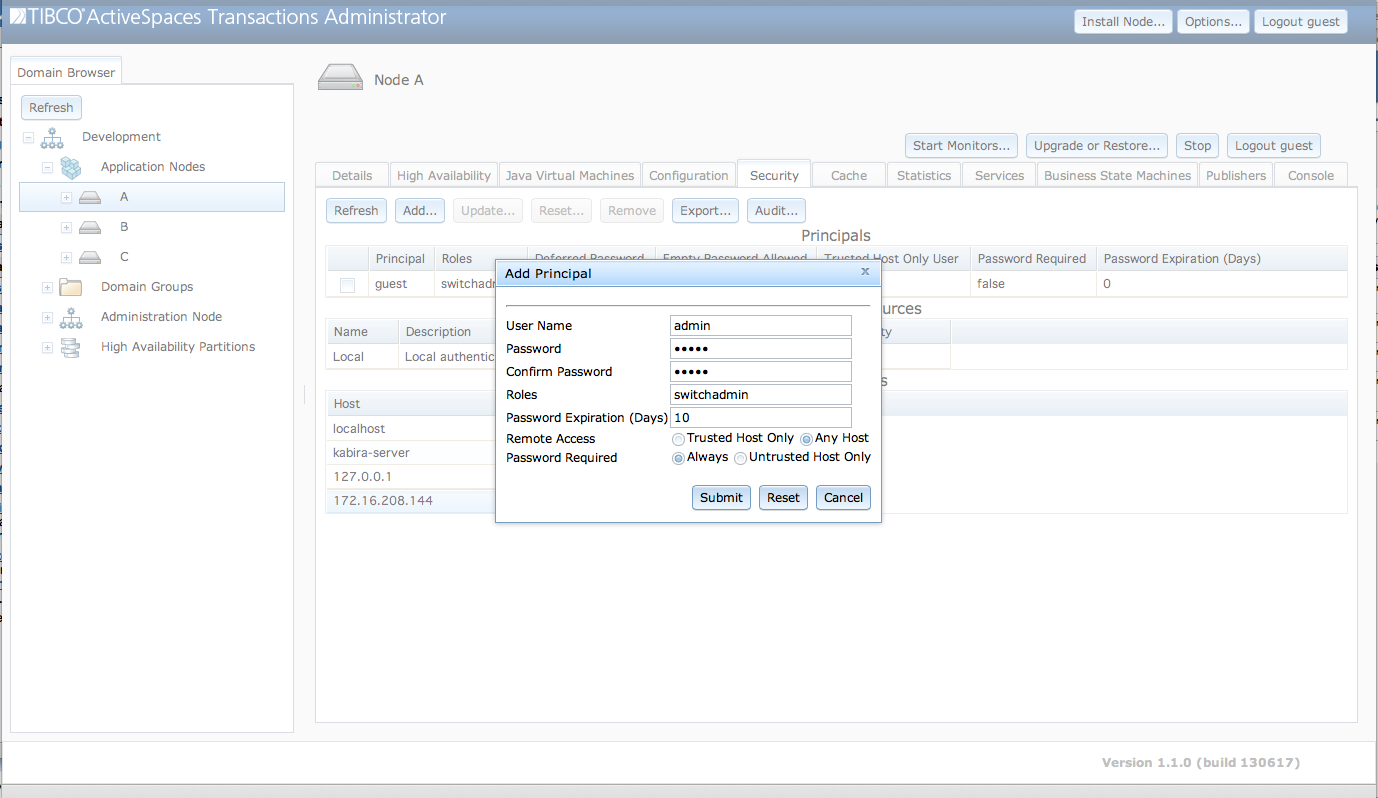
Users are added to a node's local
authentication realm using the Add Principal dialog
shown in Figure 5.5, “Add user” accessed from the
Add... button.
The fields in the Add Principal dialog
are:
User Name - A unique name for this user.
Password - Initial password for this user.
Confirm Password - Password confirmation.
Roles - A space separated list of roles to assign to this user.
Password Expiration (Days) - Password expiration in days. A value of zero indicates that the password does not expire.
Locked - Locked account setting.
Clicking on the Submit button will add the new
user to the node after validating that the password values match.
Users can also be added using:
epadmin --servicename=<node-service-name> add user \ --username=admin --password=supersecret --roles=administrator
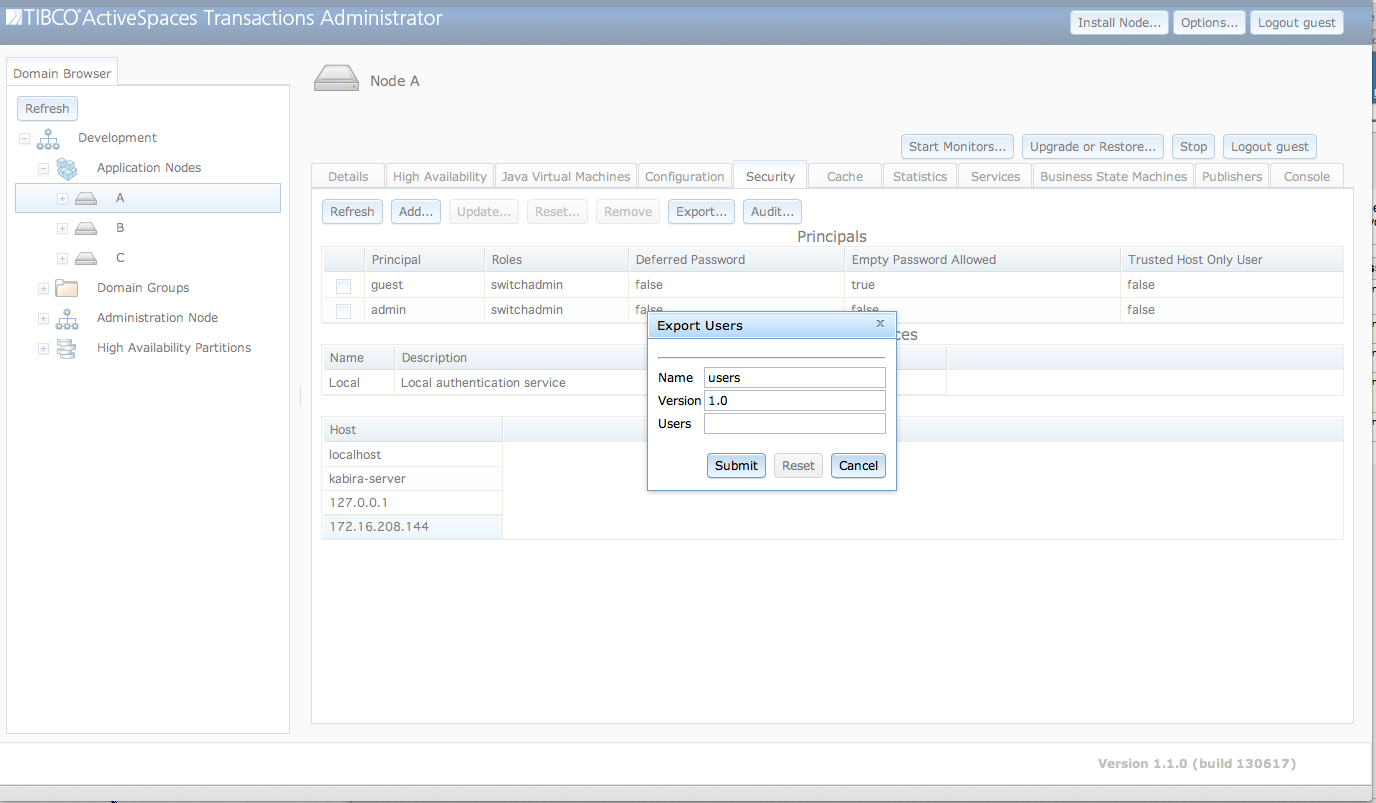
All principals defined in a local authentication realm on
a node can be backed up using the Export Users dialog
show in Figure 5.6, “Backup local authentication realm”. This dialog is
accessed from the Export... button. The realm backup
can be reloaded on a node using the restore realm administration command
(see the section called “realm target”).
The fields in the Export Users dialog
are:
Name - Local authentication realm to backup.
File - Backup to this file.
When the Submit button is clicked, the realm is
backed up to the specified file. No sensitive information, such as
passwords is visible in the exported file.
Local authentication realms can also be backed up using this command:
epadmin --servicename=<node-service-name> backup realm --name=default-realm > default-realm.backup
Local authentication realms can be restored using this command:
epadmin --servicename=<node-service-name> restore realm --name=default-realm --file=/opt/backups/default-realm.backup
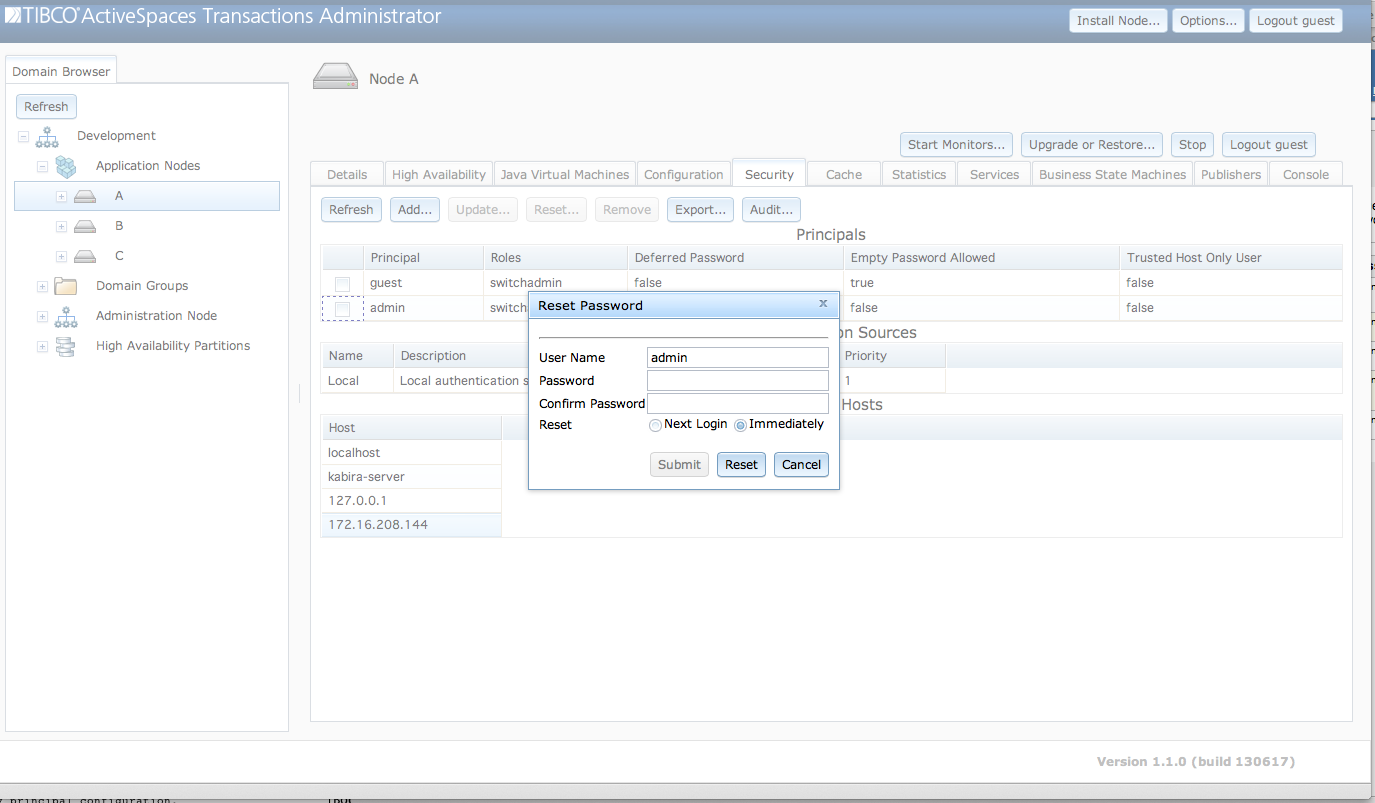
Passwords are changed in a local authentication realm
using the Reset Password dialog shown in Figure 5.7, “Change password” accessed from the
Reset... button.
The fields in the Reset Password dialog
are:
User Name - User name of password being changed. This field is read-only. It is set to the user selected in the
Principalstable.Password - New password.
Confirm Password - Confirm password.
When the Submit button is clicked the password
has been changed.
Passwords can also be changed using this command:
epadmin --servicename=<node-service-name> change password --realm=default-realm --username=admin
Users defined in a local authentication realm are removed
from a node by selecting a principal in the
Principals table as shown in Figure 5.8, “Remove user” and clicking on the
Remove button.
When the Submit button is clicked the user has
been removed.
Principals can also be removed using this command:
epadmin --servicename=<node-service-name> remove user --realm=default-realm --username=admin
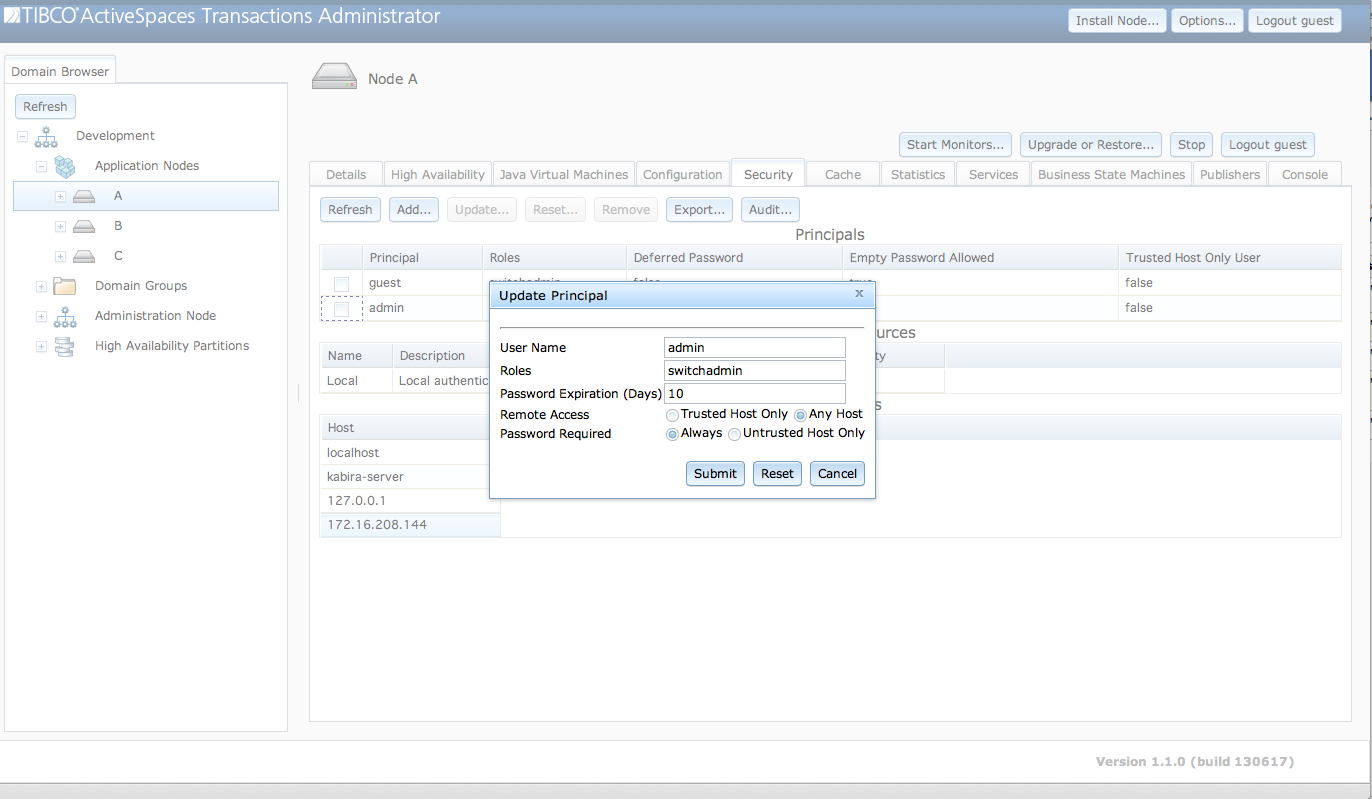
User defined in a local authentication realm are updated
using the Update Principal dialog shown in Figure 5.9, “Update user” accessed from the
Update... button.
The fields in the Update Principal dialog
are:
User Name - User name being updated. This field is read-only. It is set to the user selected in the
Principalstable.Roles - A space separated list of roles for this principal.
Password Expiration (Days) - Password expiration in days. A value of zero indicates that the password does not expire.
Locked - Optionally lock the user account.
The fields contain the current values for the user when the dialog
is initially displayed. When the Submit button is
clicked any changed values are updated for the user.
Users can also be updated using this command:
epadmin --servicename=<node-service-name> update user \
--username=admin --roles=administratorThe authentication realm associated with node administration is set by default to a local authentication realm when a node is installed (see the section called “Default security”). The default node administration authentication realm cannot be changed using configuration. For example the following fails:
//
// New configuration using an
// authentication realm name of default-realm
// (the default authentication realm name)
//
name = "my-local-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LocalAuthenticationRealm =
{
name = "default-realm"
requirePassword = false
initialPrincipals =
[
{
userName = "guest"
password = ""
roles =
[
"administrator"
]
}
]
}
}
//
// Load configuration
//
epadmin --servicename=A.X load configuration --source=realm.conf
[A.X] type = com.tibco.ep.dtm.configuration.security
[A.X] name = my-local-authentication-realm
[A.X] version = 1.0.0
//
// Activation fails because default local authentication realm
// cannot be changed
//
epadmin --servicename=A.X activate configuration \
--type=com.tibco.ep.dtm.configuration.security \
--name=my-local-authentication-realm --version=1.0.0
[A.X] Audit failed: TIBCO-EP-DTM-00277: configuration (my-local-authentication-realm, com.tibco.ep.dtm.configuration.security, 1.0.0)
contains an authentication realm with name "default-realm", which already exists in
(default-realm-config, com.tibco.ep.dtm.configuration.security, 1.0.0)However, it is possible to change the authentication realm associated with node administration to either a different local authentication realm or an LDAP authentication realm. Here are the required steps to change the node administration realm:
Load and activate a local (see the section called “LocalAuthenticationRealm”) or LDAP (see the section called “LDAPAuthenticationRealm”) realm configuration using the
configurationadministration target (see the section called “configuration target”), or as default configuration deployed with an application (see the section called “Overriding and augmenting default application and node configuration”).Use the
setadmin realmadministration command to change to the new realm (see the section called “realm target”).
This example defines a single administration user named
admin in a new local authentication realm and then
updates node administration to use this new realm.
name = "my-local-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LocalAuthenticationRealm =
{
name = "my-local-authentication-realm"
requirePassword = false
initialPrincipals =
[
{
userName = "admin"
password = "admin"
roles =
[
"administrator"
]
}
]
}
}
//
// Display the current node administration realm
// This command is using the operating system
// user that installed the node so no
// user name or password is required from a trusted host
//
epadmin --servicename=A.X getadmin realm
[A.X] Realm Name = default-realm
//
// Load the realm configuration
//
epadmin --servicename=A.X load configuration --source=realm.conf
[A.X] type = com.tibco.ep.dtm.configuration.security
[A.X] name = my-local-authentication-realm
[A.X] version = 1.0.0
//
// Activate the new realm configuration
//
epadmin --servicename=A.X activate configuration --type=com.tibco.ep.dtm.configuration.security \
--name=my-local-authentication-realm --version=1.0.0
//
// Set node administration to use this realm
//
epadmin --servicename=A.X setadmin realm --name=my-local-authentication-realm \
--newrealmuser=admin --newrealmpassword=admin
//
// Display the updated node administration realm
// The new administrator user name and password must be
// specified since admin is not the operating system user
// that installed the node.
//
epadmin --servicename=A.X --username=admin --password=admin getadmin realm
[A.X] Realm Name = my-local-authentication-realmWhen changing the node administration realm the new realm must
have at least one user defined with the administrator
role to ensure that the node can be managed in the new realm. This is
verified by the setadmin realm command by requiring
the username and password of an administration user in the new
realm.
Attempting to remove the last administration user in a local authentication realm is also prevented to ensure that a node can always by administered.
epadmin --servicename=A.X --username=admin --password=admin remove user \
--realm=my-local-authentication-realm --username=admin
[A.X] Error: TIBCO-EP-DTM-00481: "admin" is the last remaining user in the realm and cannot be removed.![[Warning]](images/warning.png) | |
There is no audit preventing the last administration user from being removed when using an LDAP authentication realm. If the last administration user is removed from the LDAP server, the node can no longer be accessed for management and must be forcefully removed using operating system facilities. |
There are cases where administrators can unintentionally lock out all node administration users. Examples are:
Remove the last user with administration privileges.
Password expires for administration user.
Explicitly lock the administration user's account.
Switch to a realm that has no administration users defined.
etc.
There are two choices at this point:
Remove the node directory and processes using operating system specific mechanisms. This causes an application outage and loss of any data stored on the node.
Use the
reset authenticationcommand to restore the default authentication set up when a node was installed (see the section called “Default security”).
To reset node authentication, the reset
authentication command is executed on the same machine on
which the node is installed. Operating system write access privileges to
the node installation directory must be available to the user executing
the command.
epadmin reset authentication --installpath=A.X
See the section called “authentication target” for more details.
Every administrative command is recorded in an audit log (see the section called “Logging”). For each command executed the audit log reports on:
the command and target executed.
the principal that executed the command.
whether the command succeeded or failed.
the failure cause, if the command failed.